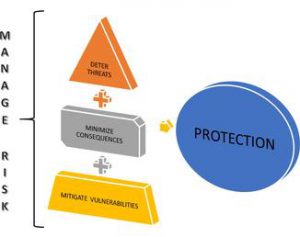
Threat, Vulnerability, and Risk Assessment (TVRA) is a comprehensive process used by organizations to identify, analyze, and evaluate potential threats, vulnerabilities, and associated risks to their assets, systems, and operations. Here’s a breakdown of each component:
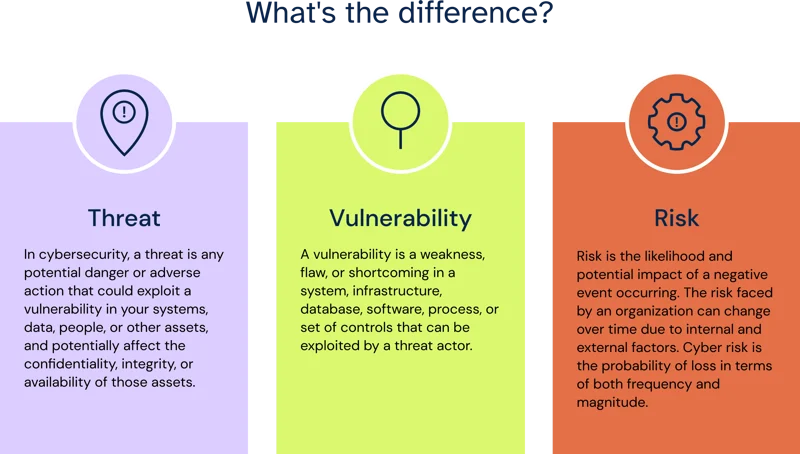
Threat: A threat refers to any potential event or circumstance that can cause harm to an organization’s assets, systems, or operations. Threats can be natural (e.g., earthquakes, floods), human-made (e.g., cyberattacks, sabotage), or environmental (e.g., power outages, equipment failures). Identifying threats involves understanding the various ways in which an organization could be compromised or disrupted.
Vulnerability: Vulnerability refers to weaknesses or flaws in an organization’s systems, processes, or controls that could be exploited by threats to cause harm. These weaknesses can exist in hardware, software, personnel, procedures, or physical infrastructure. Identifying vulnerabilities involves assessing the organization’s defense mechanisms and understanding where weaknesses may exist.
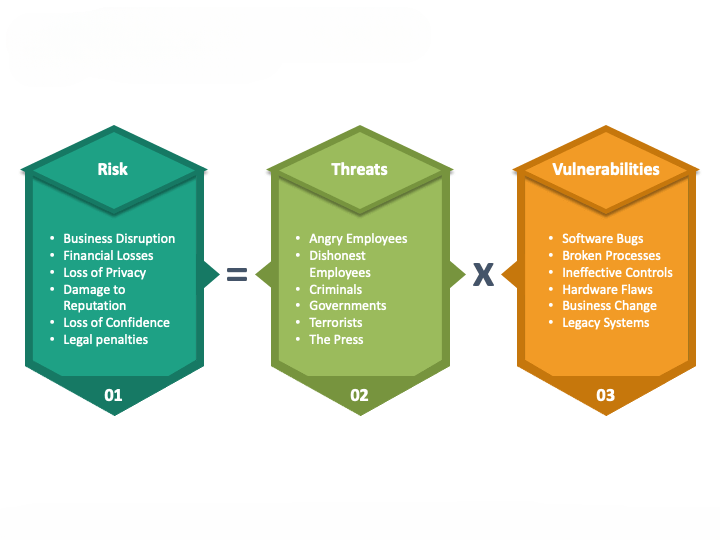
Risk: Risk is the potential for loss, harm, or damage resulting from the interaction between threats and vulnerabilities. It encompasses the likelihood of a threat exploiting a vulnerability and the impact it would have on the organization if realized. Risks can be categorized based on their severity, likelihood, and potential consequences.
There are a number of different risk assessment methodologies, including the National Institute of Standards and Technology (NIST) Special Publication 800-30, the ISO/IEC 27005 standard, and the COBIT 5 framework. Each has its own strengths and weaknesses, and no one methodology is perfect for every organization. It is important to select a methodology that meets the specific needs of your organization and that you are comfortable using.
The TVRA process typically involves the following steps:
Asset Identification: Identifying and categorizing the organization’s assets, including information assets, physical assets, personnel, and critical infrastructure.
Threat Identification: Identifying potential threats that could impact the organization’s assets, considering both internal and external sources.
Vulnerability Assessment: Assessing the organization’s vulnerabilities and weaknesses that could be exploited by identified threats.
Risk Analysis: Analyzing the likelihood and potential impact of threats exploiting vulnerabilities to determine the level of risk associated with each scenario.
Risk Evaluation: Evaluating and prioritizing risks based on their severity, likelihood, and potential impact on the organization’s operations and objectives.
Risk Treatment: Developing and implementing risk mitigation strategies to reduce, transfer, or accept identified risks based on organizational priorities and resource constraints.
Monitoring and Review: Continuously monitoring and reviewing the effectiveness of risk mitigation measures and adjusting the TVRA process as needed to address new threats or vulnerabilities.
In the assessment phase, the risks to information resources are identified and quantified. The response phase involves developing and implementing plans to reduce or mitigate the risks. The monitoring phase involves ongoing evaluation of the risk management strategy to ensure that it is effective in reducing the risks to information resources.
In today’s rapidly evolving digital landscape, safeguarding your business against potential threats is paramount. Threat Vulnerability Risk Assessment (TVRA) is not just a best practice; it’s a crucial step in fortifying your organization’s defenses and ensuring its long-term resilience.
TVRA empowers your organization to take a proactive approach to risk management. By systematically identifying and evaluating potential threats and vulnerabilities, you can anticipate security risks before they materialize into costly breaches or disruptions. This proactive stance enables you to implement targeted mitigation strategies and allocate resources where they are needed most, thereby reducing your overall risk exposure.
In an increasingly regulated environment, compliance with industry standards and regulatory requirements is non-negotiable. Many regulatory frameworks, such as GDPR, HIPAA, and PCI DSS, mandate the conduct of risk assessments as part of your organization’s compliance obligations. TVRA not only helps you demonstrate compliance with these regulations but also ensures that your security measures are aligned with industry best practices.
Your organization’s assets are among its most valuable resources. Whether it’s sensitive data, intellectual property, or operational infrastructure, protecting these assets from security threats is essential for maintaining business continuity and safeguarding your reputation. TVRA enables you to identify and prioritize critical assets, allowing you to implement targeted security controls and measures to mitigate potential risks effectively.
Informed decision-making is contingent upon a thorough understanding of your organization’s risk landscape. TVRA provides you with valuable insights into your risk profile, enabling you to make data-driven decisions about resource allocation, investment in security technologies, and strategic initiatives. By leveraging these insights, you can optimize your security posture and ensure that your organization remains agile and resilient in the face of emerging threats.
Security is not a one-time endeavor; it’s an ongoing journey. TVRA facilitates continuous improvement by establishing a framework for regular assessment and refinement of your security measures. By regularly revisiting and updating your risk assessments, you can adapt to evolving threats, technologies, and business priorities, ensuring that your organization remains ahead of the curve and resilient to emerging challenges.
We conduct thorough TVRA processes to identify and analyze potential threats, vulnerabilities, and associated risks to your organization’s assets and operations. Our assessments cover all aspects of your security landscape to provide a holistic view of your risk profile.
Based on the findings of our assessment, we develop customized risk mitigation strategies to address identified threats and vulnerabilities effectively. Our goal is to help you implement proactive measures to minimize risk and enhance your organization’s resilience to security incidents.
We ensure that our TVRA services align with industry standards and regulatory requirements, helping you demonstrate compliance with relevant regulations such as GDPR, HIPAA, and PCI DSS. Our team stays abreast of evolving regulatory landscapes to keep your organization ahead of compliance challenges.
Security threats are constantly evolving, which is why we provide ongoing monitoring and support to help you stay ahead of emerging risks. We work collaboratively with your team to implement continuous improvement strategies that strengthen your security posture over time.
We understand that every organization has unique needs and challenges. That’s why we offer customized TVRA services tailored to your specific requirements. Whether you’re a small business or a large enterprise, we provide scalable solutions that address your organization’s individual risk landscape.s.
Protect your organization from potential threats with GRC360‘s comprehensive TVRA services. Contact us today to schedule a consultation with our team and take the first step towards enhancing your security posture and safeguarding your business.
© All rights reserved@GRC360