A Cybersecurity Maturity Assessment (CSMA) is a comprehensive evaluation designed to measure the effectiveness and maturity of an organization’s cybersecurity program. The primary objectives of a CSMA are to:
By conducting a CSMA, organizations can develop a clear roadmap for improving their security measures, mitigating risks, and ensuring ongoing compliance with relevant regulations and standards.
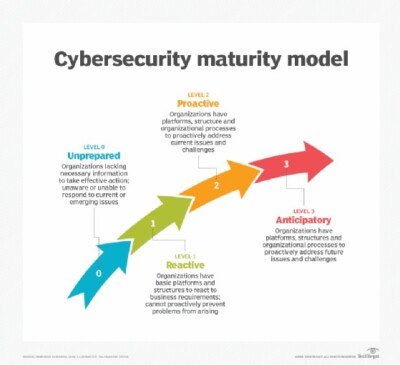
The Cybersecurity Maturity Assessment focuses on specific controls that protect critical assets, infrastructure, applications,
and data by assessing your organization’s defensive posture. The assessment also emphasizes operational best practices for
each control area, as well as the organizational effectiveness and maturity of internal policies and procedures.
The Cybersecurity Maturity Assessment focuses on specific controls that protect critical assets, infrastructure, applications,
and data by assessing your organization’s defensive posture. The assessment also emphasizes operational best practices for
each control area, as well as the organizational effectiveness and maturity of internal policies and procedures.
The CSMA assesses compliance with several industry requirements, as well as the following control sets and frameworks:
Each of these control frameworks map to one another and are designed to provide a structure with which a security program
can measure its maturity and effectiveness—now and for the future
A Cybersecurity Maturity Assessment (CSMA) is essential for organizations aiming to fortify their cybersecurity posture and ensure robust protection against evolving threats. Here are key reasons why you need a CSMA:
Identify Vulnerabilities and Gaps: A CSMA helps pinpoint weaknesses in your current cybersecurity setup, allowing you to address vulnerabilities before they can be exploited by malicious actors.
Improve Risk Management: By understanding the maturity of your cybersecurity practices, you can better manage and mitigate risks, prioritizing resources and efforts where they are needed most.
Strategic Planning and Investment: A CSMA provides insights that inform your cybersecurity strategy, helping you make informed decisions about where to invest in technology, training, and resources.
Enhance Compliance: Aligning your security program with industry standards and best practices through a CSMA ensures you meet regulatory requirements and avoid penalties associated with non-compliance.
Boost Stakeholder Confidence: Demonstrating a commitment to cybersecurity maturity enhances trust and confidence among customers, partners, and investors, showcasing your organization’s dedication to protecting sensitive information.
Facilitate Continuous Improvement: A CSMA is not a one-time effort but a continuous process that fosters an environment of ongoing improvement, ensuring your cybersecurity practices evolve with emerging threats and technologies.
Benchmark Against Peers: Understanding how your organization’s cybersecurity maturity compares to industry peers provides valuable context and helps identify areas for improvement and competitive advantage.
Support Business Objectives: By aligning cybersecurity efforts with business goals, a CSMA ensures that security measures support and enable the overall mission and objectives of the organization.
At GRC360, we offer a comprehensive suite of services designed to enhance your organization’s cybersecurity posture through our Cybersecurity Maturity Assessment (CSMA).
We conduct a thorough assessment of your current cybersecurity measures to identify strengths and weaknesses. This evaluation includes:
Our experts provide an unbiased review of your existing security strategies and plans. This service involves:
We help you develop actionable plans to enhance your cybersecurity maturity. This includes:
We ensure your security program aligns with industry best practices and meets regulatory requirements. This involves:
Our assessments are customized to meet the specific needs of your organization. We provide:
At GRC360, our goal is to help you identify vulnerabilities, manage risks, and ensure your cybersecurity measures are robust and aligned with your business objectives. Through our comprehensive CSMA services, we empower your organization to proactively protect against threats and enhance your overall security posture.
© All rights reserved@GRC360